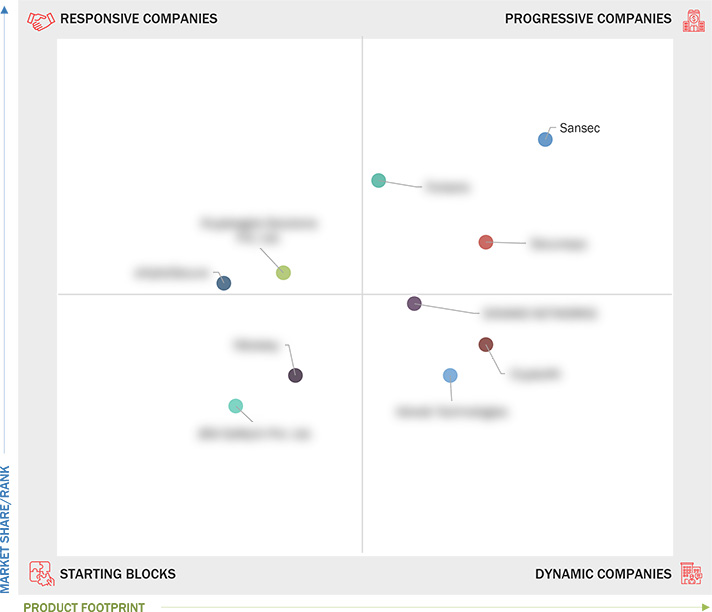
Comparing 10 vendors in Hardware Security Modules Startups across 0 criteria.
Become a Client
- Access Exclusive Reports, expert insights and tailored support to drive growth.
Summary
The hardware security module (HSM) market is pivotal in providing robust cryptographic protection to safeguard keys and accelerate encryption processes. As the digital economy expands, the necessity for secure handling of sensitive data across numerous platforms has become urgent, particularly with the rising incidences of data breaches and cyber threats. A hardware security module is essentially a cryptoprocessor dedicated to managing cryptographic keys and streamlining encrypted operations. Functioning typically as plug-in cards or standalone network devices, HSMs offer essential services such as key generation, storage, encryption acceleration, and secure backup of confidential data.
The HSM market is experiencing significant growth driven by several factors, including the exponential increase in digital transactions and the adoption of stringent data security regulations across critical sectors like banking, healthcare, and government. The market is highly dynamic, characterized by a blend of well-established market leaders and innovative startups. Key players such as Thales, Utimaco, IBM, and Futurex dominate by leveraging both organic strategies—like product innovations—and inorganic strategies, including acquisitions of smaller firms.
Moreover, the market is being reshaped by technological trends and disruptions, such as cloud computing and Internet of Things (IoT) technologies, which demand advanced security solutions. Advances in quantum computing and blockchain technologies further emphasize the HSMs' role as a cornerstone in securing modern digital infrastructures. In this fiercely competitive landscape, continuous innovation and adoption of new technologies define the strategic priorities for companies seeking to maintain a competitive edge and secure a larger market share.
Startup Descriptions
Sansec (China): Sansec, a progressive SME, offers customized HSM solutions that are pivotal in securing digital communications and data across numerous platforms. They actively engage in strategic growth initiatives to expand their market presence.
Fortanix (US): Known for its innovative product portfolio, Fortanix operates as a startup focused on delivering advanced security solutions, including robust HSM services for diverse industry needs.
Securosys (Switzerland): Securosys specializes in securing digital assets with its Primus HSM products, providing enhanced security features for financial services and beyond.
DINAMO NETWORKS (Brazil): This dynamic startup offers innovative HSM products, focusing on expanding their reach through effective channel partnerships and reseller networks.
ellipticSecure (UK): As a responsive company, ellipticSecure develops cutting-edge security modules designed to meet future demands in digital security.
Kryptoagile Solutions Pvt. Ltd. (India): With a focus on responsive product solutions, Kryptoagile is expanding its portfolio to strengthen its market position.
Crypto4A (Canada): Crypto4A offers dynamic HSM solutions, supported by government collaborations, to provide secure cryptographic services.
Nitrokey (Germany) Operating in the starting blocks, Nitrokey focuses on innovating new products to establish a stronger market presence in the HSM sector.
Adweb Technologies (India): Positioned as a dynamic company, they aim to bolster their market footprint through extensive innovation and robust channel partnerships.
JISA Softech Pvt. Ltd. (India): Engaged primarily in developing new technologies, JISA represents a budding startup focused on enlarging its sales capabilities and market influence.
1 INTRODUCTION
1.1 Study Objectives
1.2 Market Definition
1.3 Study Scope
1.3.1 Markets Covered and Regional Scope
1.3.2 Inclusions and Exclusions
1.3.3 Years Considered
1.4 Currency Considered
1.5 Unit Considered
1.6 Stakeholders
1.7 Limitations
1.8 Summary of Changes
2 MARKET OVERVIEW
2.1 Introduction
2.2 Market Dynamics
2.2.1 Drivers
2.2.1.1 Increasing data breaches and cyberattacks
2.2.1.2 Need to comply with stringent data security regulations and
standards
2.2.1.3 Growing demand for effective management of cryptographic
keys
2.2.1.4 Transition to digital transactions and electronic payments
2.2.1.5 Shift toward SDN and NFV in 5G deployments
2.2.2 Restraints
2.2.2.1 High ownership costs associated with hardware security
modules
2.2.2.2 Susceptibility to cyberattacks and security breaches
2.2.3 Opportunities
2.2.3.1 Rising volume of data generated by websites and mobile apps
2.2.3.2 Proliferation of connected devices and IoT technologies in
smart cities
2.2.3.3 Rise of telemedicine and remote healthcare services
2.2.3.4 Increasing adoption of blockchain and cryptocurrencies
2.2.3.5 Advancements in quantum computing
2.2.4 Challenges
2.2.4.1 Discovering and protecting sensitive data
2.2.4.2 Complexities associated with HSM integration process
2.2.4.3 Rise of complex IT environments
2.3 Trends/Disruptions Impacting Customer Business
2.4 Pricing Analysis
2.4.1 Average Selling Price Trend of HSMs, By Key Player
2.4.2 Average Selling Price Trend of HSMs, By Type
2.4.3 Average Selling Price Trend of Lan-Based/Network-Attached HSMs,
By Region
2.5 Supply Chain Analysis
2.6 Ecosystem Analysis
2.7 Technology Analysis
2.7.1 Key Technologies
2.7.1.1 AI and ML
2.7.1.2 Contactless smart cards
2.7.1.3 Quantum safe hardware security modules
2.7.2 Complementary Technologies
2.7.2.1 PKI
2.7.3 Adjacent Technologies
2.7.3.1 Blockchain and distributed ledger technologies
2.7.3.2 Digital signatures
2.8 Patent Analysis
2.9 Trade Analysis
2.9.1 Import Data (HS Code 8471)
2.9.2 Export Data (HS Code 8471)
2.10 Key Conferences and Events, 2025–2026
2.11 Case Study Analysis
2.11.1 Epx Achieved Future-Proof Payment Processing Infrastructure with
Futurex’s Excrypt Series
2.11.2 Fortanix Helped It and Networking Company with Dsm Saas That
Offered Robust and Consistent Security across Global Operations
2.11.3 Futurex Helped Pomelo Implement Robust Cloud-Based Payment
Infrastructure
2.11.4 Stanchion and Futurex Assisted Israeli Bank with Secured Payment
Environments
2.11.5 Thales Luna HSMs Helped Bangladesh’s IDTP with Enhanced Security
and Allowed Secure Real-Time Movement of Funds
2.11.6 Thales Helped Treezor Deploy Cloud HSM That Provided Every
Customer with Exclusive HSM Service
2.12 Investment and Funding Scenario
2.13 Tariff and Regulatory Landscape
2.13.1 Tariff Analysis
2.13.2 Regulatory Bodies, Government Agencies, and Other Organizations
2.13.3 Standards
2.14 Porter’s Five Forces Analysis
2.14.1 Threat of New Entrants
2.14.2 Threat of Substitutes
2.14.3 Bargaining Power of Suppliers
2.14.4 Bargaining Power of Buyers
2.14.5 Intensity of Competitive Rivalry
2.15 Key Stakeholders and Buying Process
2.15.1 Key Stakeholders in Buying Process
2.15.2 Buying Criteria
2.16 Impact of Ai on Hardware Security Modules Market
3 COMPETITIVE LANDSCAPE
3.1 Introduction
3.2 Key Player Strategies/Right to Win, 2020–2024
3.3 Revenue Analysis, 2020–2023
3.4 Market Share Analysis, 2024
3.5 Company Valuation and Financial Metrics, 2024
3.6 Brand/Product Comparison
3.7 Company Evaluation Matrix: Key Players, 2024
3.7.1 Stars
3.7.2 Emerging Leaders
3.7.3 Pervasive Players
3.7.4 Participants
3.7.5 Company Footprint: Key Players, 2024
3.7.5.1 Company footprint
3.7.5.2 Region footprint
3.7.5.3 Type footprint
3.7.5.4 Technology footprint
3.7.5.5 Deployment type footprint
3.7.5.6 Application footprint
3.7.5.7 Vertical footprint
3.8 Company Evaluation Matrix: Startups/SMEs, 2024
3.8.1 Progressive Companies
3.8.2 Responsive Companies
3.8.3 Dynamic Companies
3.8.4 Starting Blocks
3.8.5 Competitive Benchmarking: Startups/SMEs, 2024
3.8.5.1 Detailed list of key startups/SMEs
3.8.6 Competitive Benchmarking of Key Startups/SMEs
3.9 Competitive Scenario
3.9.1 Product Launches/Developments
3.9.2 Deals
3.9.3 Expansions
3.9.4 Other Developments
4 COMPANY PROFILES
4.1 SECUROSYS
4.1.1 Business overview
4.1.2 Products/Solutions/Services offered
4.1.3 Recent developments
4.2 ADWEB TECHNOLOGIES
4.2.1 Business overview
4.2.2 Products/Solutions/Services offered
4.2.3 Recent developments
4.3 ELLIPTICSECURE
4.3.1 Business overview
4.3.2 Products/Solutions/Services offered
4.3.3 Recent developments
4.4 SANSEC
4.4.1 Business overview
4.4.2 Products/Solutions/Services offered
4.4.3 Recent developments
4.5 FORTANIX
4.5.1 Business overview
4.5.2 Products/Solutions/Services offered
4.5.3 Recent developments
4.6 JISA SOFTECH PVT. LTD.
4.6.1 Business overview
4.6.2 Products/Solutions/Services offered
4.6.3 Recent developments
4.7 NITROKEY
4.7.1 Business overview
4.7.2 Products/Solutions/Services offered
4.7.3 Recent developments
4.8 KRYPTOAGILE SOLUTIONS PVT. LTD.
4.8.1 Business overview
4.8.2 Products/Solutions/Services offered
4.8.3 Recent developments
4.9 CRYPTO4A
4.9.1 Business overview
4.9.2 Products/Solutions/Services offered
4.9.3 Recent developments
Latest
Crypto4A Technologies Inc. Introduces Quantum-Safe HSM Platform Software Version 4.4
 Dec 2024
Dec 2024 einpresswire
einpresswireFortanix Tackles Quantum Computing Threats With New Algorithms
 Feb 2025
Feb 2025 Dark Reading
Dark ReadingCompany List